About Deceptive Bytes
Deceptive Bytes provides an innovative solution against threats in enterprises’ most critical and exposed assets, their endpoints! The solution is a fully endpoint-centric prevention/deception platform that creates dynamic & deceiving information, responds to the evolving nature of advanced threat landscape and interferes with attackers attempts to recon the environment that deters them from executing their malicious intents, through all the stages of compromise in the Attack Kill Chain – covering advanced & sophisticated malware techniques, constantly making sure all the endpoints & data in the enterprise are secured.
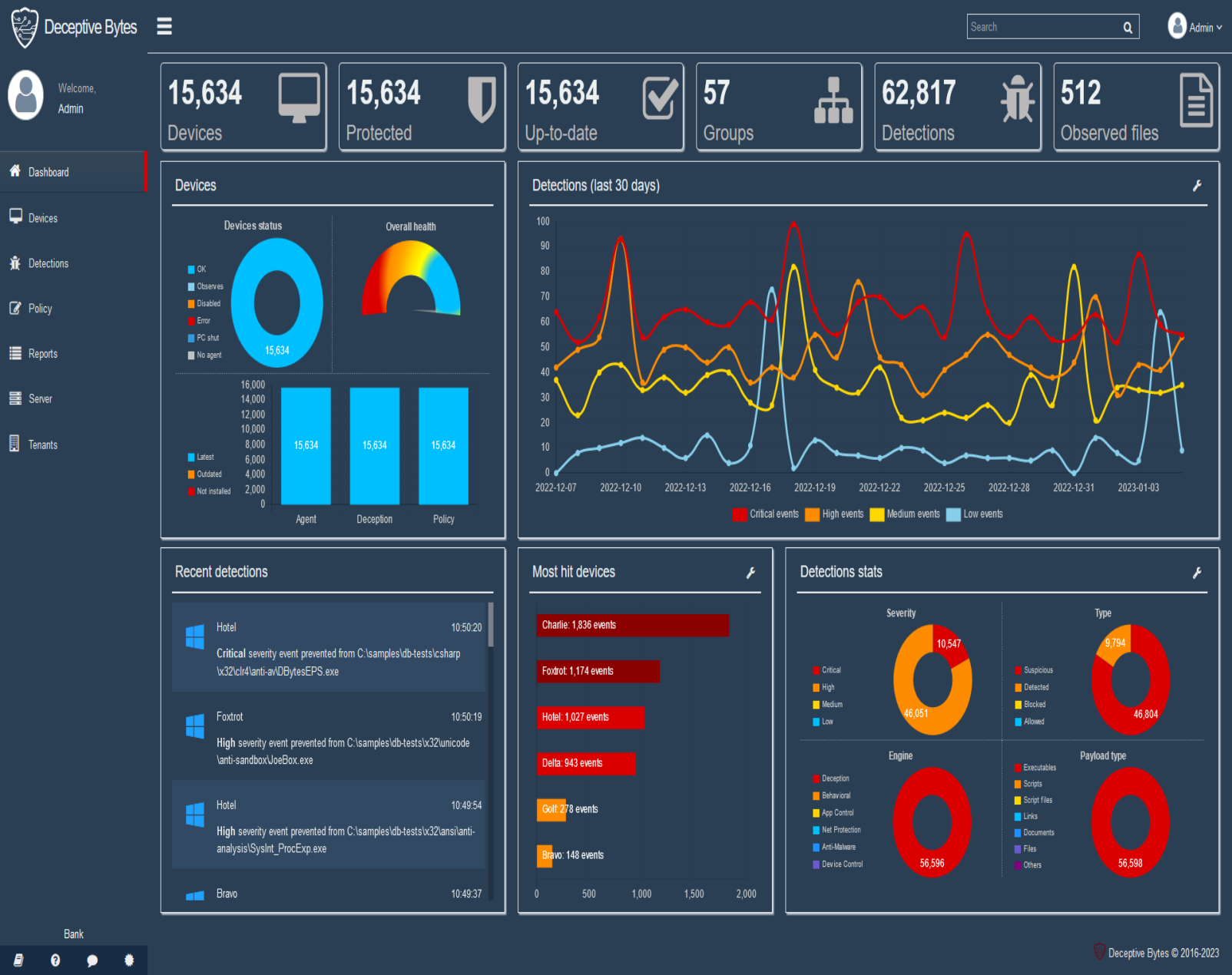
Solution Engine: Stop Malware In Its Tracks.
Deception
Making malware believe it’s in an unattractive/hostile environment to attack & actively responding to it as it evolve - changing its outcome.
App Control
Manages applications execution, allowing or blocking apps according to policy.
Anti-malware
Controls Windows Defender settings on the endpoint through the management server and receive detections to it.
Behavioral
Protects legit applications used for malicious attacks.
Network Defense
Controls Windows Firewall configuration on the endpoint.
Device Control
Manages security for connected devices
Threat Intel
Blocks known threats using web gathered information.


